Is Your Payment Data Being Sent to China?
This is the question many companies are asking after Keith Rabois’ accusations against Airwallex
👋 I am a tech lawyer that breaks down all of the fun and complex legal topics that companies should be aware of.
So…Where Exactly Is Our Payments Vendor?
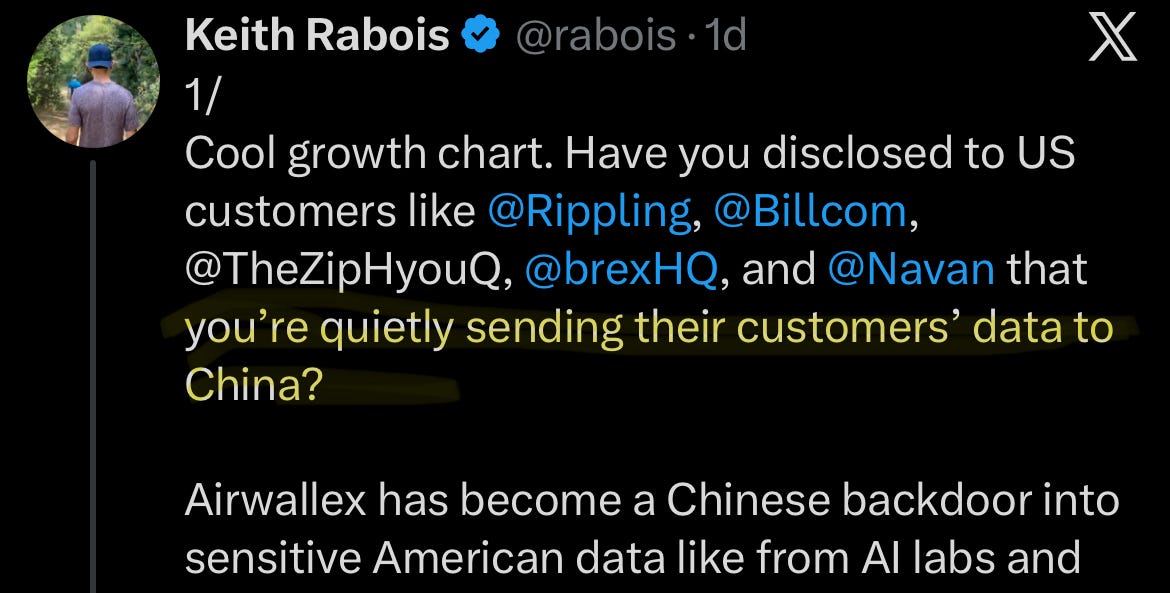
Keith Rabois, VC at Khosla Ventures, kicked off a firestorm on Twitter/X this week by publicly accusing a major global payments provider (Airwallex) of being an unintended data pipeline into China.
The kind of tweet that makes half of tech Twitter go silent, and makes every CISO immediately open their laptop like they’re defusing a bomb.
Before we go any further, let’s get something clear before we go any further:
These are allegations, not proven facts.
But the reason the post spread faster than a phishing scam is because it hits a nerve companies never want to talk about: If your vendor has people, systems, or entities in another country, then that country’s laws apply to your data.
It’s not espionage. It’s not intrigue. It’s jurisdiction.
(Which is somehow less fun than espionage but way more dangerous.)
The Part Companies Pretend Isn’t Relevant
Public info tells us the Airwallex has:
HQ in Singapore
Big engineering + ops teams in mainland China and Hong Kong
A China-regulated payments license
Major Chinese investors
None of this is misconduct. But it’s absolutely relevant.
Because if your vendor operates, or has its decision makers or engineers, in a foreign jurisdiction, then the laws of that jurisdiction come attached like a warranty nobody reads.
The Chinese Law Everyone Tiptoes Around
China’s National Intelligence Law (2017) says individuals and organizations must:
“support and cooperate with national intelligence work,”
and…
“keep that cooperation confidential.”
Add the Data Security Law and Cybersecurity Law, and you now have a country with authority over:
data stored in China
infra operated from China
companies regulated in China
employees physically sitting in China, even if serving foreign customers
Legal scholars call this a broad scope of authority.
CEOs call it “Wait…what?”
The U.S. Government Is Paying Attention Too
The U.S. already dropped a legal anvil on this earlier this year: The 2024 Executive Order on Protecting Americans’ Sensitive Data
The EO directs DOJ, DHS, Treasury, and Commerce to block or restrict U.S. data from flowing into “countries of concern,” specifically including China.
The EO flags:
financial transactions
payroll data
employee PII
corporate payments
anything revealing supply chains or operational patterns
You know…the exact things your payments provider processes every minute.
The EO doesn’t ban these vendors outright. But it screams: “At least know who’s touching your data.”
Why This Story Exploded: Everyone Realized They Might Not Know
Most vendor reviews are basically:
SOC 2?
ISO cert?
Pen test?
“Very professional-sounding” security questionnaire answers?
Meanwhile no one is asking:
“So…where are your production engineers physically located?”
“Which country’s laws apply to them?”
“Where does our data go when something breaks at 3 AM?”
“Can a foreign government legally demand access and would we ever be told?”
“Is the failover region somewhere we’ve never discussed?”
This is how companies discover “accidentally” that their payroll vendor sends logs to a city no one can pronounce, or their payments processor uses offshore contractors to debug fraud alerts.
I once reviewed a contract where the vendor proudly advertised “U.S-only data processing,” and then casually mentioned their Shanghai engineering team had “support visibility.”
Support visibility is a lovely phrase that translates to: “full access.”
Where This Gets Legally Messy
Not hypothetical. Real problems:
Your privacy notices may be flat-out wrong. If you said “data stays domestic,” and it doesn’t, that’s a violation, sometimes a major one.
Your contract won’t save you. No DPA overrides national intelligence law.
Regulators will ask very specific questions. “Where is this processed?” cannot be answered with “regionally.”
Boards absolutely hate international surprises. Especially involving payroll or payments.
Your cyber insurer will raise your premiums. Underwriters already ask about offshore access. Now they’ll underline it.
The Questions Every Company Should Ask, Today
If you ask nothing else, ask these:
Who has production access, and where are they located? Actual teams. Actual cities.
Where is our data processed, backed up, and mirrored? If they send a marketing diagram, you already have the answer.
Are any of your employees required to comply with foreign intelligence laws? You’ll know by the pause.
Can you guarantee that encryption keys never leave approved jurisdictions? This is where most vendors get nervous.
Can you notify us if any government requests access? In some countries, the answer is legally “no.”
Do your investors have information rights that could expose our data indirectly? This one separates the adults from the interns.
What to Say When Your CEO Slacks You the Tweet
Use this:
We’re not assuming the tweet is accurate. But the underlying issue applies to any vendor with operations in certain jurisdictions. We’re reviewing where our vendors’ access and processing actually occur.
It shows control without panic. Boards love that.
The Actual Point Here
You don’t need to know whether the tweet was right or wrong.
You just need to know this: If you don’t understand where your vendor’s people and systems are, you don’t understand where your data is.
And in 2025, that’s not a small detail…
Footnotes:
Reply to this email with any legal topics you want to read about!
Share this newsletter with your friends.
*Nothing in this post is legal, investment, tax, or financial advice. This is for educational purposes only.